Checksums Unleashed: Safeguarding Software Integrity
Checksums: Ensuring Integrity Checksums are vital for verifying the integrity of downloaded software. They are unique strings generated by an algorithm that reflect the file’s content.Checksums: Ensuring Integrity Checksums are vital for verifying the integrity of downloaded software

Let’s delve into the world of checksums and their significance in ensuring the integrity of downloaded software.
The Importance of Verifying Software with Checksums
What’s a Checksum?
A checksum is a short, unique string generated by an encryption algorithm on a given file. This algorithm examines all the bits that make up the file and creates a checksum based on those unique bits. Even a single bit change in the file will alter the checksum. Comparing two checksums, we can verify whether a file has been tampered with or corrupted.
Why Use Checksums?
File Integrity Assurance:
When you download large binary files (like software), there’s a chance of bit errors during transmission. These errors can occur for various reasons, such as network glitches or incomplete downloads.
A single-bit error might seem insignificant, but it can propagate and cause issues. For instance:
Imagine downloading an ISO file and burning it onto a DVD to install Linux. During setup, the installer detects a broken file on the disk. This could be due to a single-bit error during the download.
Verifying the checksum ensures that the downloaded file matches the original, preventing such errors.
Security and Authenticity:
Suppose you’re downloading software from a mirror site (not the original creator’s server). In such cases, the source's checksum acts as a digital fingerprint.
If the checksum of your downloaded file doesn’t match the expected value, it indicates either:
- The file has errors (as discussed above).
- Someone attempts to deceive you (e.g., a compromised download site).
How to Verify Checksums
- Checksum Methods:
- MD5 and SHA (Secure Hash Algorithm) are standard checksum methods.
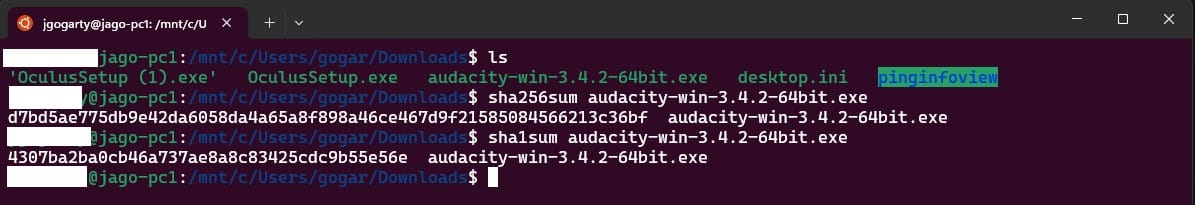
- On Windows and Linux systems, use
md5sumorsha1sumcommands to check MD5 or SHA checksums.
- Mirror Sites and Checksums:
- Many projects distribute software via mirror sites (created by various individuals).
- The checksum provided on the original site can verify that the downloaded software matches the original, even when using mirror sites.
- This is essential for security and trust, especially if the mirror site is compromised.
Common Checksum Algorithms
MD5 (Message Digest Algorithm 5):
- Produces a 128-bit checksum.
- Widely used but considered weak due to vulnerabilities.
- Still used for legacy purposes.
- Example:
d41d8cd98f00b204e9800998ecf8427e(checksum for an empty file).
SHA-1 (Secure Hash Algorithm 1):
- Generates a 160-bit checksum.
- Also considered weak due to vulnerabilities
- Deprecated for security-critical applications.
- Example:
da39a3ee5e6b4b0d3255bfef95601890afd80709(checksum for an empty string).
SHA-256 (Secure Hash Algorithm 256):
- Produces a 256-bit checksum.
- Stronger and widely used.
- Preferred for security-sensitive tasks.
- Example:
cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e(checksum for “Hello, World!”).
How to Verify Checksums
Within Windows Comand line:
In the examples below, I will be testing on Audacity to test the Checksum after downloading the software.
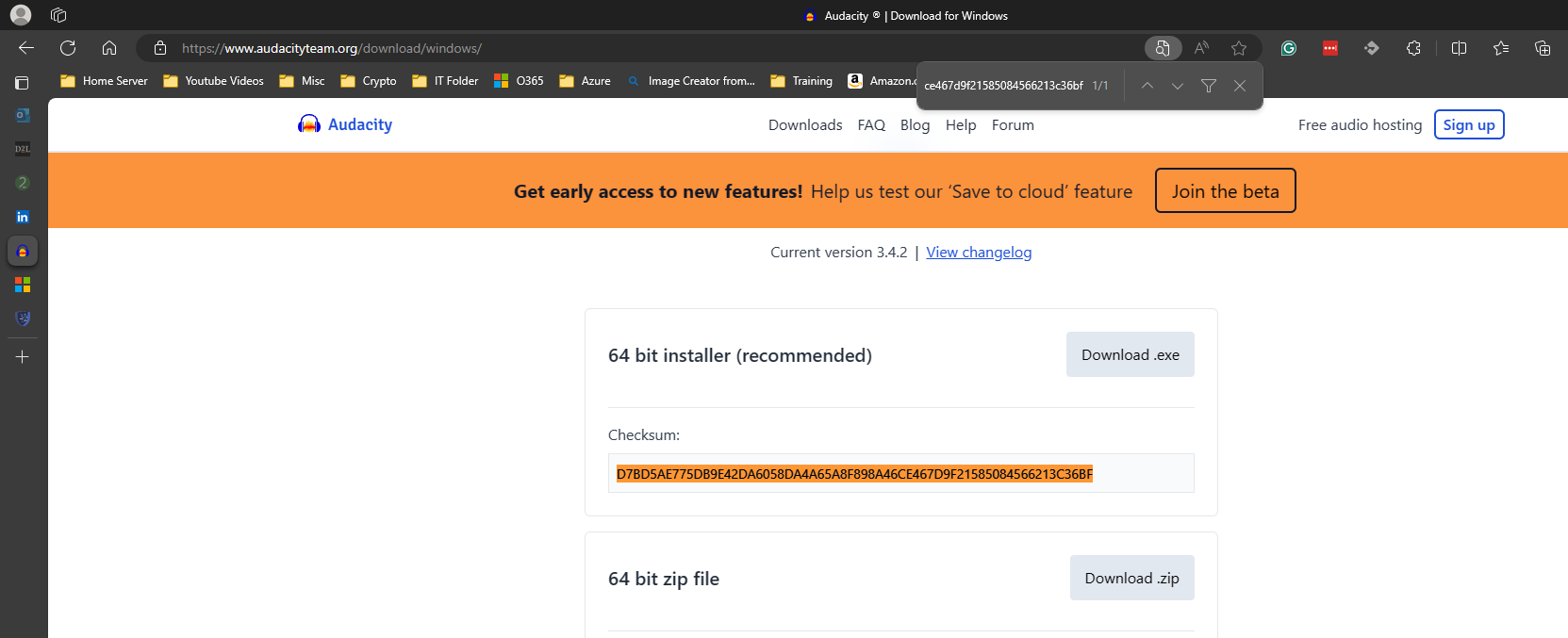
MD5: D7BD5AE775DB9E42DA6058DA4A65A8F898A46CE467D9F21585084566213C36BF
Here is another example of the MD5 and SHA-1 on the Veeam site.
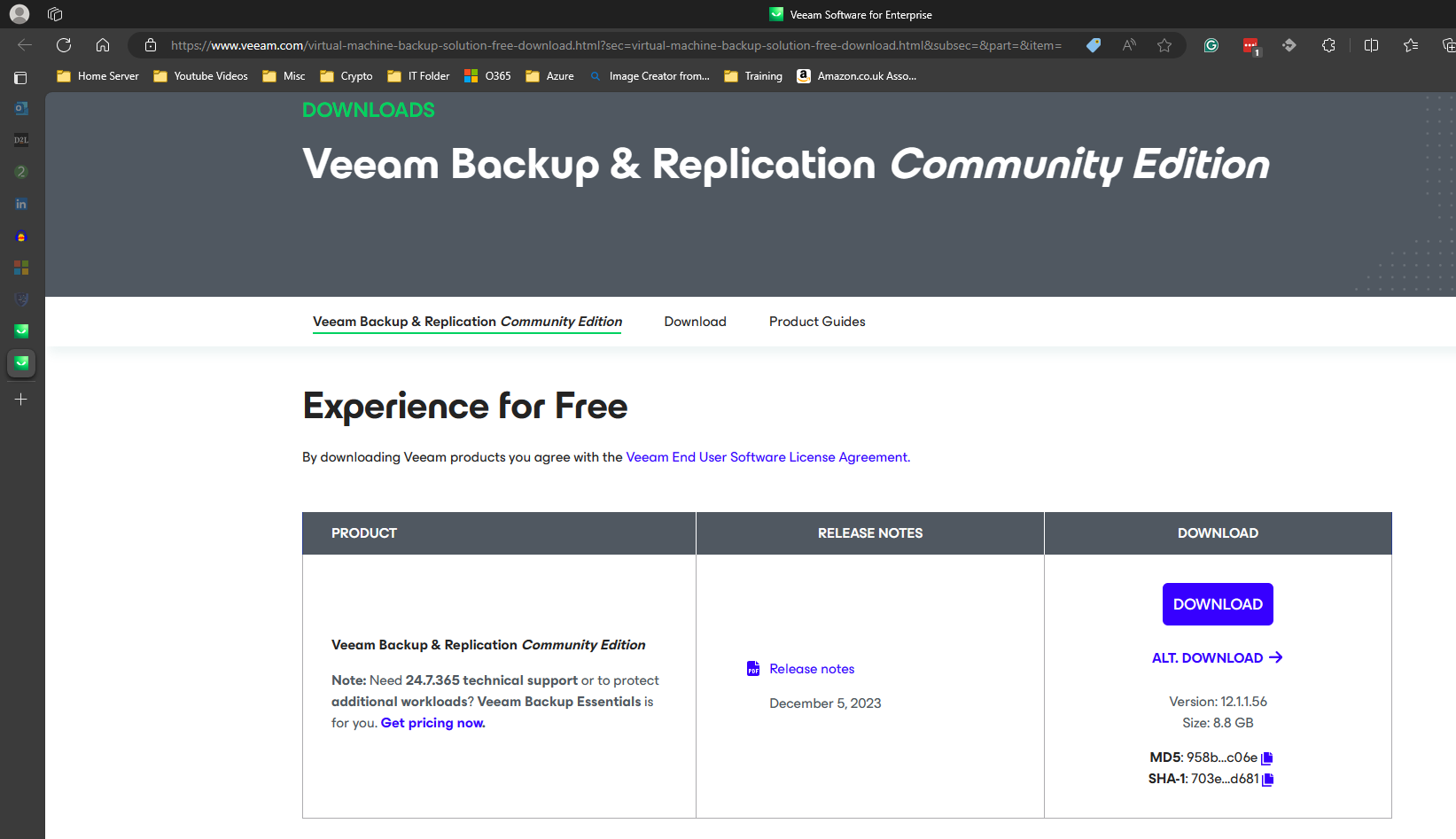
MD5: 958b10fc6590d9838aae1a257cb8c06e
SHA-1: 703ec0e771d9da46313cfde25a417d47cf74d681